Featured Downloads

The Preventative, Developer-Driven Approach to Software Security
The focus on automation, tooling and reactive responses to cyber threats can no longer stand alone against an increasingly sophisticated threat landscape, where attackers are also employing advanced tools to successfully breach even the most protected networks and systems. What ... Read more

Future Frontiers: Why Developers Need to Go Beyond the OWASP Top 10 for Secure Coding Mastery
In 2021, we usher in a new era for the fabled OWASP Top 10. This latest release reveals some significant shake-ups, with Injection flaws finally being toppled from the top spot in favor of Broken Access Control vulnerabilities. Brand new ... Read more

OWASP Top 10 API: Strategies for Smart Developers
Threats to cybersecurity these days are ubiquitous and relentless. It’s become so bad that trying to keep up with them after programs are deployed has become almost impossible. However, in this age of DevSecOps, continuous delivery, and more data paydirt ... Read more
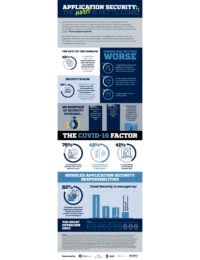
Application Security: The Best/Worst Is Yet to Come
In the wake of recent high-profile breaches, all eyes are on application security. Yet, application security hasn’t always received the attention during the application development process it deserves. Many organizations deploy applications with known vulnerabilities to meet their deadlines, with ... Read more

Adopting a Strategic Mindset for Cloud-Native Application Protection
With more applications being developed in a cloud-native fashion, using containers and serverless architecture, organizations should think about smarter, more efficient and more reliable ways to protect their applications. Cyberattackers are more innovative and are achieving more success in compromising ... Read more

Identity: The Real Key to Security
Identity and access management (IAM) has long been touted as an effective way to ensure data security by providing access only to those who have the correct permissions. In today’s increasingly distributed IT environment, more organizations look for zero-trust computing ... Read more
Security Boulevard Library
Welcome to our library of security-related resources. Here you will find whitepapers, ebooks, and more – all that will help you in your security journey. Access requires only a free registration. Search, scroll through and download what you like.

Threat & Attack Surface Intelligence (ASI): See What Adversaries See and Stop Them in KNOW Time (Resolution Brief)
Threat and Attack Surface Intelligence from Netenrich addresses the major reasons attacks still succeed: Fast-growing digital footprint Threat actors see things you don’t Skills gaps and shortages Fast-changing threat landscape Find out how you can continuously shrink your attack surface, act on critical threats and stay “in the KNOW” as threats ... Read more
Netenrich

What Makes Intelligence Actionable and Worth Your Time?
In and of itself, finding assets at risk on the Internet is not that exciting or overly helpful. Assigning a risk score and prioritizing risks based on relevant context, however, saves you a ton of time. To be truly actionable, intelligence should get you to the point where you know ... Read more
Netenrich

Enough With the Data Already!
True “resolution intelligence” moves the needle on a challenge by taking you from data through intelligence to action to prevent or remediate a problem for good. Learn how both threat and attack surface intelligence can resolve your attack surface, today and over time ... Read more
Netenrich

Everything You Need to Know About Cyber Threats — In Minutes, Free
Even with enough cybersecurity experts to go around, you never have time to stay on top of all the news. Until now. Or should we say, until KNOW? Knowledge NOW (KNOW) makes it easy to dig deep into breaking news, evolving trends, and the threats and IOCs that matter to ... Read more
Netenrich

Threat & Attack Surface Intelligence (ASI): See What Adversaries See and Stop Them in KNOW Time
Netenrich uniquely delivers continuous adversary insight by integrating threat and attack surface intelligence to prevent risk, streamline operations and bridge skills gaps — in less time, and without creating more work for your own team ... Read more
Netenrich

Multi-Cloud Data Security: Cloud Security Landscape
According to Gartner, 81% of enterprise businesses are adopting either a hybrid cloud or a multi-cloud strategy to drive business agility. Based on the Cloud Threat Report 2019 released by Oracle and KPMG, 71% of data now in the public cloud is “sensitive.” As workloads and sensitive data move to ... Read more
Fortanix

The Buyer’s Guide to Penetration Testing: Vendor Checklist
In today’s IT environment, one of the biggest risks to a corporation’s valuation is a security breach. But, how does a security team apply their budget in a way that ensures the applications, websites and other assets are secure? Security vendors make wide claims about the effectiveness of their products ... Read more
Synack

The Buyer’s Guide to Penetration Testing
Breaches are all too common today as determined cyber criminals have become better organized and more targeted in their attacks. In many cases, a C-level executive loses their job as a result. That doesn’t have to be you or your organization. The right testing solution is key to keeping you ... Read more
Synack

Why Zero Trust Should Be at the Forefront of Your IAM Strategy
With IT security, trust has always been a critical element. Now, with digital transformation and cloud adoption increasing among organizations, implementing security specific to the network perimeter has evolved. IT security teams need to enable access rights for users regardless of their location, device or network. Utilizing the Zero Trust ... Read more
ManageEngine

The State of Cloud Native Security 2020
The first annual State of Cloud Native Security report examines the practices, tools and technologies innovative companies are using to manage cloud environments and drive cloud native development. Based on a survey of 3,000 cloud architecture, InfoSec and DevOps professionals across five countries, the report surfaces insights from a proprietary ... Read more
Palo Alto Networks

